9 Enterprise Cybersecurity Best Practices for Ultimate Protection
by Madhu Reddiboina | Feb 9, 2023 | IAM

The 9 Essential Enterprise Cybersecurity Best Practices for Ultimate Protection
In this blog post, we’ll dive into the most effective ways to fortify your organization against cyber criminals, ensuring your business remains safe and secure.
Why Is Enterprise Cybersecurity So Important?
There’s no denying the increasing number of data breaches and cyber-attacks are a serious threat – increasing globally by 125% from 2020 to 2021
Implementing cybersecurity best practices is the only way for security teams to effectively protect an organization from potential harm.
The risk of not getting your cybersecurity right is too significant, with IBM reporting that the average cost of a data breach in the United States is $9.44 million.
9 Best Practices For Enterprise Cybersecurity
Let’s jump into the 9 best practices that we recommend you start implementing today:
- Effectively define your scope
- Audits: Assess and Eliminate Your Company’s Vulnerabilities
- Utilize end-to-end data protection
- Take advantage of your enterprise architecture
- Choose an Appropriate Identity and Access Management (IAM) Solution
- Conduct regular cybersecurity training
- Implement strong password policies
- Have a Cohesive Incident Response Plan in Place
- Work with a reputable managed security service provider
1. Effectively Define Your Scope
Successful cybersecurity all boils down to effective preparedness. Having a clear-cut scope for your cybersecurity strategy ensures smooth operations.
But why is it so important for enterprises in particular?
In a large organization, there are any number of moving parts – multiple teams, made up across departments, working across different elements of projects all at the same time. The scope of your cybersecurity program has to take into account all of those moving parts to protect your organization while not inhibiting any of that day-to-day work and cross-departmental collaboration.
That’s why failing to define your scope for cybersecurity upgrades or improvements in enough detail can have a huge negative result on implementation.
A well-defined scope that falls in line with the wider goals of the business and supports crucial daily operations ensures that there’s a clear prioritization of resources – eliminating the possibility of the project being under, or over-resourced.
For best practices on defining your scope of cybersecurity efforts, check out our article on the NIST cybersecurity framework
2. Audits: Assess and Eliminate Your Company’s Vulnerabilities
Generally speaking, the best way to improve a company’s security is to find and fix its weakest links.
So how exactly do we do that?
By conducting regular, thorough security audits and assessments.
The first step is identification – identifying all possible threats that could have an impact on your organization. This could be anything from network breaches to phishing attacks, or maliciously planted malware.
Now it’s time to put the current security to the test by running vulnerability scanning and penetration testing on your current security.
By simulating a real-world attack on the company, any immediate weaknesses in the system can be identified. This is a form of red team testing that utilizes ethical hacking techniques in an attempt to take advantage of any weaknesses and penetrate a cybersecurity system – reporting on their findings if successful.
Want to find and fix the weaknesses in your cybersecurity system? Get in touch today to speak to a RediMinds Fraud Red Testing Expert about how we can help.
With all threats identified, it’s time to carry out a risk assessment to evaluate the likelihood of each identified threat occurring and the impact on the company’s most critical data.
No system is 100% impenetrable, meaning vulnerabilities to some degree will always appear and need to be dealt with – and some threats will be more dangerous than others. The crucial thing here is the prioritization of potential threats to tackle the most critical weaknesses first.
3. Utilize End-To-End Data Protection
Implementing end-to-end protection is an approach used to secure data from unauthorized access – preventing potential alterations or loss of data.
End-to-end protection is integral to any enterprise cybersecurity because it helps protect sensitive information, meet compliance requirements, prevent data breaches, and maintain business continuity.
End-to-end is really the last line of defense in a cybersecurity system. In the event of a data breach, the idea is that the encrypted data adds an extra layer of security such that the data is not readable.
4. Take Advantage of Your Enterprise Architecture
Having a comprehensive view of an organization: its structure, processes, and data flows allows for a seamless upgrade to any cybersecurity system.
Having this structure mapped out clearly can be utilized to identify and prioritize potential security threats. Incorporating security into the architecture of a company ensures that security is integrated into all aspects of the organization.
When implementing any new cybersecurity improvements, it’s critical to keep the entire architecture of the company in mind to guarantee seamless implementation.
5. Choose an Appropriate Identity and Access Management (IAM) Solution
IAM is a system designed to identify, authenticate and authorize. This enables the right employees and job roles in an organization to have access to the right tools they need to do their work at the right time.
This is best practice for creating a separation of duties and responsibilities that’s vital to enterprises in order to:
- Conform to regulatory compliance
- Reduce human error
- Streamline IT workflows
- Improve data security
- Improve data confidentiality
- Detect insider threats in real-time
6. Conduct Regular Cybersecurity Training
In a new world that relies so heavily on technology, it’s easy to forget about the basics – human input.
In fact, it’s reported that 95% of cybersecurity breaches are actually caused by human error, according to the world economic forum. A statistic far too staggering to ignore.
There’s no denying the importance of keeping your teams up to scratch with cybersecurity training. Be sure to check out our article on employee cybersecurity training for our round-up of tips to make your training more effective.
7. Implement Strong Password Policies
Implementing strong password policies is critical for any enterprise cybersecurity program.
The importance of having a strong password is often overlooked in organizations and left to the employees, hence the staggering statistic that 80% of data breaches are linked to a weak password.
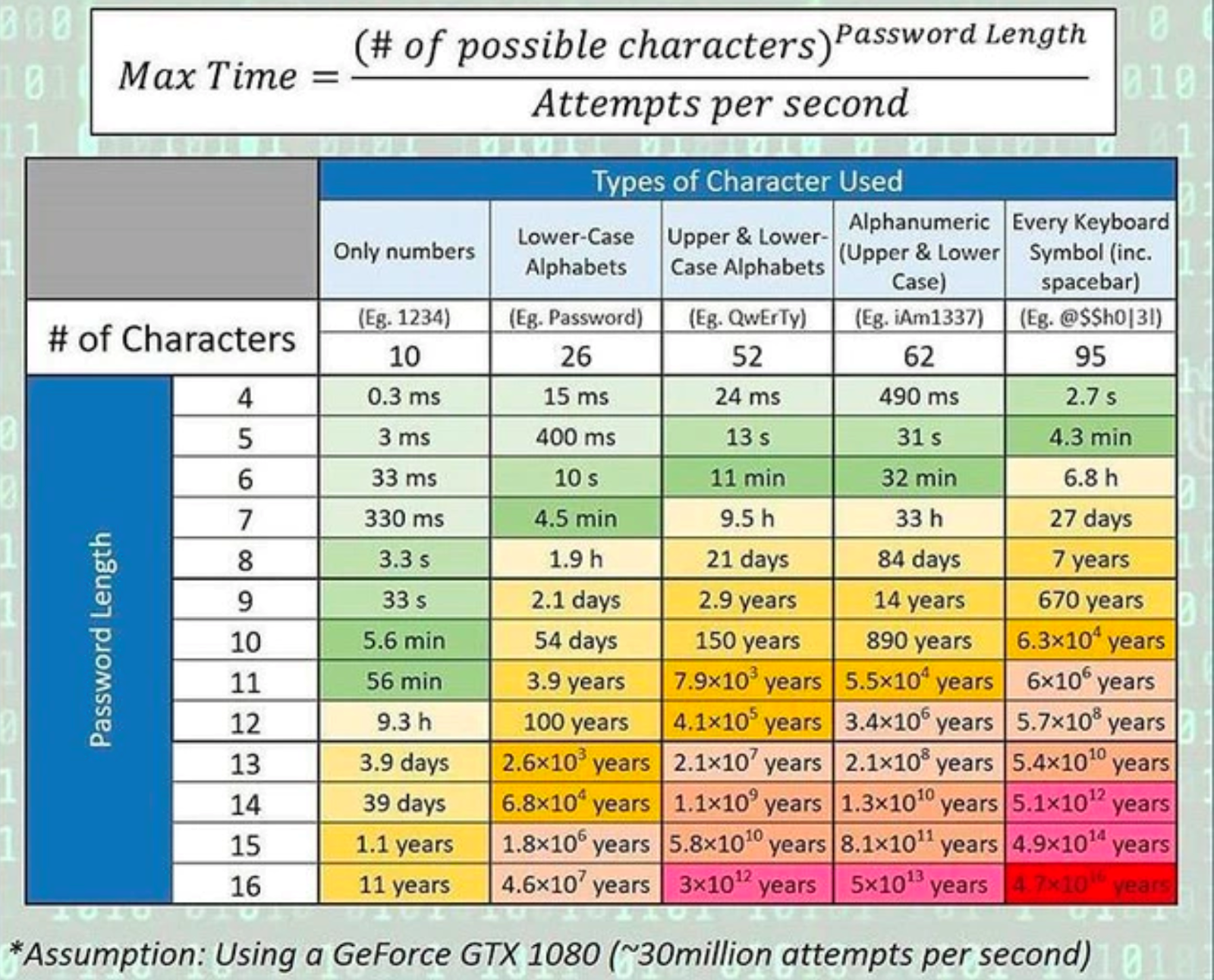
To really appreciate the importance of a strong password, just take a look at how much longer it would take a hacker using brute force tactics to guess a password of 16 characters, using every keyboard symbol (47,000,000,000,000,000 years) versus just 4 numbers (0.3 milliseconds).
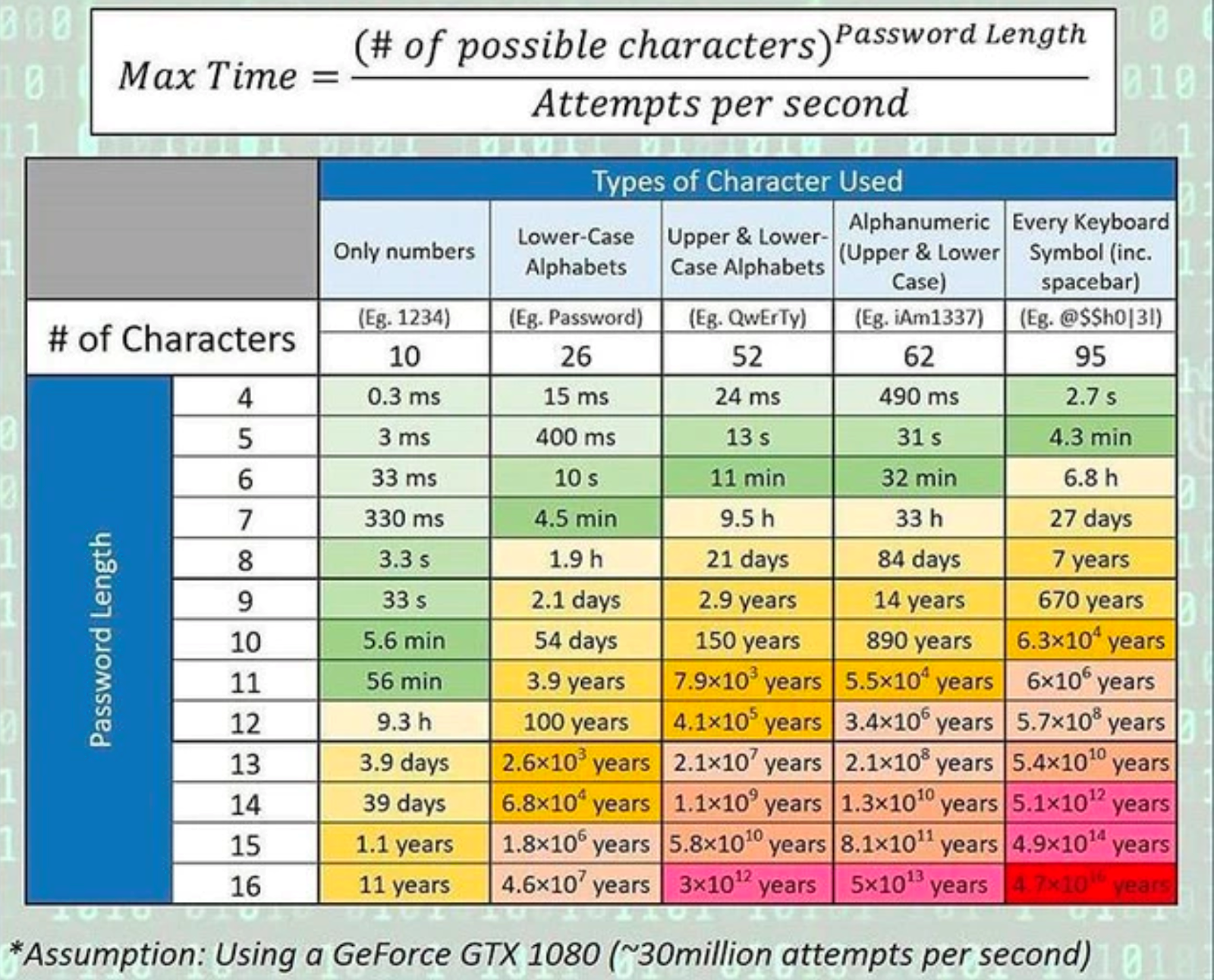
(Photo credit: University of South Wales)
We have an entire article on password best practices to cover this in more detail.
Have a Cohesive Incident Response Plan in Place
Clear steps to take in the event of a security breach or other cybersecurity incident is critical to any enterprise cybersecurity program.
An effective incident response plan will include
Defined roles: The responsibilities of team members in each department in the event of an incident
Evidence preserving: Including the procedure for collecting information such as logging system activity, preserving hard drives, and retaining relevant communications
Communication protocols: Reporting and updating stakeholders such as employees, customers, and regulatory authorities
Containment and mitigation procedures: The set of actions that will be taken to limit the impact of an incident such as isolating an infected system and disabling compromised accounts
Having a well-developed incident and response plan in place enables organizations to minimize the impact of a security breach by acting quickly and effectively when the time comes.
9. Work With a Reputable Managed Security Service Provider
Cybersecurity requirements are now so complex that they’ve often outgrown the expertise of even the most well-developed internal IT teams. In fact, Sophos found that 54% of companies state cyberattacks are too advanced for their IT teams to handle on their own.
It’s common practice for an organization to seek an outside service provider to help monitor and respond to threats.
Rediminds are a certified security implementation partner for the most reliable of those solutions, Okta and Transmit security. So, whether you’re looking for help with your fraud prevention or identity and access management solution, get in touch today and find out how Rediminds can help!