IAM & PAM: The Security Duo Your Business Needs – RediMinds
by Madhu Reddiboina | Mar 22, 2023 | IAM

IAM & PAM: The Security Duo Your Business Needs
One way to achieve this is by implementing Identity and Access Management (IAM) and Privileged Access Management (PAM) solutions. While often viewed as an “either or”, PAM is actually a subset of IAM and the two solutions work cohesively under the right circumstances.
IAM is a set of policies, processes, and technologies that ensure that only authorized individuals have access to an organization’s resources, systems, and data. This is achieved by managing user identities, authentication, and authorization.
PAM, on the other hand, is a security practice focused on managing privileged accounts that have elevated access and permissions to an organization’s most critical systems and data.
In today’s digital landscape, organizations face increasing threats from cyber criminals, making it imperative to protect your organization from both external and internal threats. IAM and PAM solutions help mitigate these risks by providing centralized control and management of user access to sensitive data, systems, and applications.
In this article, we’ll explore the key differences between IAM and PAM, their benefits, and best practices for implementation along with common use cases for both security solutions.
IAM vs PAM: Key Differences
IAM and PAM are two distinct but complementary security solutions that help organizations manage access to their digital assets. Understanding the key differences between these two solutions is essential to selecting the strategy that best suits an organization’s needs.
IAM is an umbrella term that covers all the policies, processes, and technologies used to manage user identities and their access to an organization’s systems, applications, and data.
PAM is a subset of IAM that focuses on managing and securing privileged accounts that have access to sensitive data and critical systems.
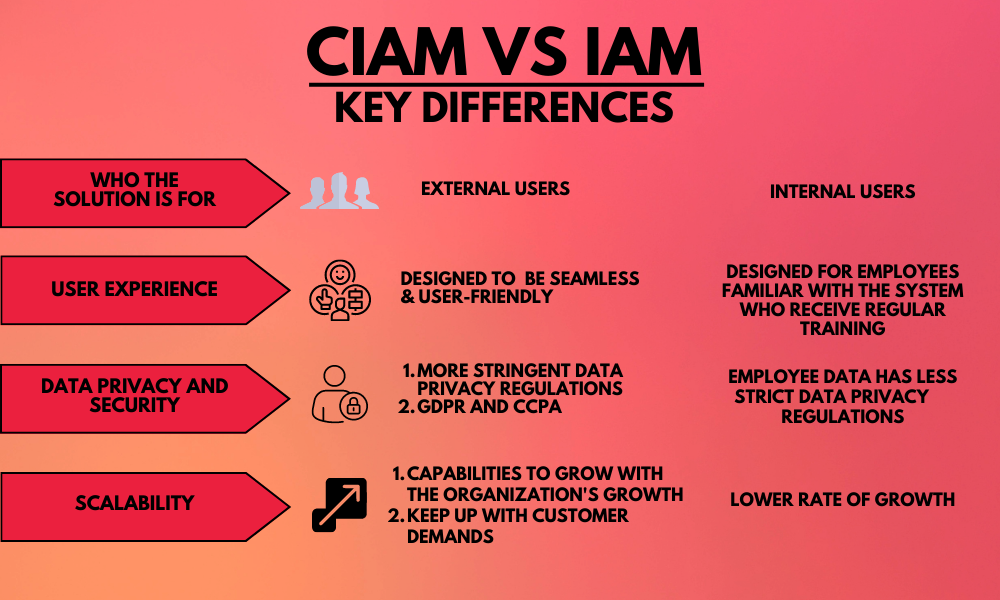
The main difference between the two solutions is who they are for.
IAM is primarily concerned with managing access to systems and data for all users and members.
PAM is specifically concerned with employees who require more privileged access – employees such as IT, high-level executives, and finance and HR teams. PAM solutions typically provide granular control over privileged accounts which are commonly targeted in spear phishing attempts.
That’s not to say that there is never some overlap in their uses. For example, when a regular user requires temporary elevated access to sensitive data or systems, PAM systems come into play.
IAM Benefits and Best Practices
IAM solutions have become an essential tool over the years. Organizations of all sizes and complexities should be implementing IAM at some level to manage and secure their digital assets effectively.
In this section, we’ll explore the benefits of IAM and best practices for implementing an effective IAM strategy.
Benefits of IAM
Improved security: IAM solutions provide a robust security framework that aids organizations in mitigating the risk of data breaches and cyber-attacks. This is achieved by controlling access to the organization’s system and information – something that’s increasingly important as more employees access an organization’s system from the edge of the network i.e. employees using mobile devices and personal networks whilst working from home.
Enhanced productivity: IAM solutions can automate previously cumbersome tasks like provisioning and deprovisioning users and managing user access to different systems and applications. This allows IT teams to focus on more pressing tasks.
Compliance: IAM solutions help organizations comply with various regulatory requirements. Compliance with regulations such as HIPAA, and GDPR is made easier when only authorized users can access sensitive data.
Best Practices for Implementing IAM Solutions
Define clear objectives: Define your organization’s objectives and priorities for IAM implementation. Objectives include enhancing security, improving productivity, and reducing costs.
Develop a comprehensive IAM strategy: Develop an IAM strategy that’s in line with objectives your organization has defined as critical. This is achieved by considering the organization’s priorities and taking into account existing infrastructure, systems, and applications.
Choose the right IAM solution: Choose an IAM solution that aligns with your organization’s needs, budget, and goals. When choosing the right IAM solution for your organization it’s important to consider factors such as scalability, ease of use, and vendor support.
If you need help selecting the right IAM solution for your organization, arrange a consultation with our team today.
We’re a trusted implementation partner for leading IAM solutions providers and can guide you in the direction that’s right for your organization.
Check out our detailed article on IAM best practices for more information.
IAM Use Cases
Employee IAM: Employee IAM solutions are designed to manage users that require access to internal systems and applications like email, file servers, and HR applications.
Customer IAM: Customer IAM solutions are designed to manage users who require access to external systems and applications including e-commerce platforms and online banking portals.
Partner IAM: Partner IAM solutions are designed to manage user access to partner systems and applications, such as supply chain management platforms and vendor portals.
PAM Benefits and Best Practices
Privileged Access Management (PAM) provides several benefits to an organization – helping them to manage, control and monitor privileged access effectively.
Let’s take a look at the benefits and best practices of PAM.
Benefits of PAM
Improved security: PAM helps to mitigate the risk of privileged account misuse and reduces the attack surface of an organization. It helps to prevent unauthorized access to critical assets and sensitive data.
Compliance: PAM helps organizations comply with regulatory requirements such as HIPAA and GDPR.
Operational efficiency: PAM helps streamline the privileged access management process and reduce the workload of IT teams. PAM solutions enable them to manage access requests, approvals, and revocations more efficiently, with proper procedures and often automations in place to support the processes.
Best Practices for Implementing PAM
Discover and catalog all privileged accounts: Perform a thorough audit to discover all the privileged accounts throughout the organization. This can be used to create an inventory of all the accounts and assign owners for each account.
Enforce strong password policies: Implement strong password policies for privileged accounts, including password complexity requirements, rotation policies, and multi-factor authentication.
Implement a least-privilege model: A common practice for PAM is to implement privileges to users based on their job roles and responsibilities. Implement the principle of least privilege and limit access to only those necessary to perform the job.
Regularly review access rights: Like all cybersecurity measures, PAM is no one-and-done activity. Access rights require periodic review to ensure that users have access only to what they need. This allows for unnecessary access rights and permissions to be removed from users who don’t require them to complete their job, for example those who may have changed job roles.
PAM Use Cases
Cloud infrastructure management: PAM helps to manage and secure privileged access to cloud infrastructure such as AWS, Azure, and GCP.
Database administration: PAM helps to manage privileged access to an organization’s sensitive databases. This reduces the risk of data breaches by reducing the total number of users accessing critical information.
DevOps and IT operations: PAM helps to manage privileged access for DevOps and IT teams, providing granular access control, session recording, and audit trails.
Speak to one of our specialist IAM experts about how RediMinds can help improve your cybersecurity and identity and access management solutions.
IAM vs PAM: FAQs