
IAM vs CIAM: Which Solution is Best for Your Enterprise Security?
Identity and access management (IAM) and customer identity and access management (CIAM) are two key technologies that enable organizations to manage user identities, control access to resources, and enhance security.
In this article, we’ll explore the differences between CIAM and IAM, their functionality and benefits, and common use cases.
What is IAM?
Identity and Access Management (IAM) is a comprehensive framework that covers the entire identity lifecycle management process. This includes policies, processes, and technologies ensuring that only authorized individuals can access an organization’s applications and resources.
Functionality and Benefits of IAM
The main functionality of IAM is to ensure users can access only the applications and resources that they’re authorized to do so.
This is achieved by implementing a range of technologies and processes like authentication, authorization, and auditing.
A successful IAM program offers multiple benefits to an organization:
Enhanced security
By controlling who has access to what resources and under what conditions the resources can be accessed, IAM can prevent sensitive information from falling into the wrong hands – ultimately improving the cybersecurity of the organization.
Increased efficiency
IAM solutions offer the ability to automate several processes that were previously time-consuming for IT teams. Processes like user provisioning and de-provisioning and running daily weekly and monthly reports. This frees up time for IT teams for more pressing matters and reduces the possibility of human errors.
Regulatory compliance
IAM ensures that organizations comply with regulatory requirements for data access and protection.
Types of IAM Systems Available
Since the pandemic, we’ve seen a significant shift in how businesses operate, with more and more businesses adopting cloud and hybrid systems.
IAM systems are available for all three system types:
On-premises: This type of IAM system is installed on the organization’s physical servers and managed internally.
Cloud-based: This type of IAM system is hosted by a third-party provider and accessed via the internet.
Hybrid: This type of IAM system combines both on-premises and cloud-based IAM solutions, providing organizations with the flexibility to choose the best approach for their needs – A very popular option for businesses adopting the work-from-home movement
RediMinds are a certified security implementation partner to both Okta and Transmit Security who offer cloud-based IAM and CIAM solutions.
Get in touch to speak to one of our experts today.
Key Features of IAM to Keep In Mind
When looking to implement an IAM system, or assessing how effective your current IAM systems are, here are some key features to keep in mind:
Authentication: The process of verifying a user’s identity, whether it be passwordless via biometrics, a physical token like a swipe card, or a traditional username and password.
Authorization: The process of granting or denying access to resources based on a user’s role and predefined permissions.
User provisioning: The process of creating, updating, and deleting user accounts.
Audit and reporting: The ability to monitor user activity and generate automated reports on user access and activity – this can be taken one step further with modern IAM systems that operate with artificial intelligence. Machine learning models are trained to detect any abnormal behavior on the system, determine a threat level, and report any threats in real-time.
How Exactly Does IAM Improve Security?
Now there’s no denying the benefits a successful IAM system can bring to a company. Let’s go over the three main areas that improve an organization’s security:
Controlling access to resources: The whole concept of IAM is to ensure that only users with authorized access can access certain company resources. This by itself is what makes IAM so beneficial – by reducing the risk of unauthorized access that can lead to security breaches.
Enforcing policies and standards: IAM enables organizations to enforce company-wide policies and standards for user access, password strength, employee training, and other security-related details.
Automating processes: By enabling automation of mundane tasks previously carried out by IT professionals gives them extra time to focus on more pressing matters. Freeing up time to strengthen any weaknesses in the organization’s cybersecurity systems, conducting audits, and fraud testing the systems to identify areas for improvement.
What is CIAM?
Customer Identity and Access Management (CIAM) is a specialized subset of IAM that focuses on managing the identities and access of customers or external users of your product or service.
CIAM solutions are designed with user experience top of mind, specifically for customer-facing applications, meaning CIAM solutions have a different set of criteria and priorities when compared to IAM solutions that are designed for employees.
Functionality and Benefits of CIAM
Similar to a successful IAM solution, the implementation of a successful CIAM solution has incredible benefits and functionalities that can be brought to your business. Some of which are:
Registration and Profile Management
One key functionality of CIAM is to enable users to create and manage their own profiles. This includes the ability to update personal information, access controls, and security preferences.
Social Identity Integration
One of the main objectives of any CIAM solution is to improve the user experience by making registration, login, and account management as seamless as possible.
Some CIAM solutions integrate with social media platforms, allowing customers to use their social media credentials to log in and access resources.
Personalization and Customization
CIAM solutions have the option to provide personalized experiences for customers, based on their preferences, history, and other factors.
Multi-Factor Authentication
CIAM solutions provide additional layers of security, such as multi-factor authentication and AI-powered adaptive authentication that use contextual behavioral analytics and administratively defined policies to decide what authentication is required under a specific set of circumstances.
Ultimately, protecting customer identities and data to the best of an organization’s ability.
Compliance and Regulatory Requirements
CIAM solutions help organizations comply with data protection regulations, such as GDPR and CCPA. These regulations determine how an organization collects, stores, and shares personal data.
A well-thought-out CIAM solution ensures compliance by providing features such as data subject access requests and consent management.
How Can CIAM Improve Customer Experience?
Given that the main objective of a successful CIAM solution is to improve the user and customer experience as much as possible, here are 3 areas of a CIAM solution that achieve this:
Providing a seamless login experience: CIAM solutions have the option for single sign-on. A feature being utilized very effectively by Google – it allows a user to sign into one application and automatically be signed into a suite of other applications. For example, when a user signs into Gmail, they’re automatically signed into Youtube, Google Drive, and any other G-suite application.
Authentication Options: CIAM solutions allow for a variety of multifactor authentication options, giving users the freedom to decide what authentication methods are most convenient for them.
Streamlining the registration process: CIAM solutions simplify the registration process, allowing customers to quickly and easily create their profiles and access resources. Given that the conversion rate of a website in 2022 was 3.65%, any improvements that can be made to the registration process have the possibility of improving this number greatly.
Overall, CIAM is a crucial technology for organizations that have customer-facing applications and services. By providing a secure and seamless user experience, CIAM solutions can help organizations build customer loyalty, increase engagement, and improve their bottom line.
CIAM vs IAM: Key Differences
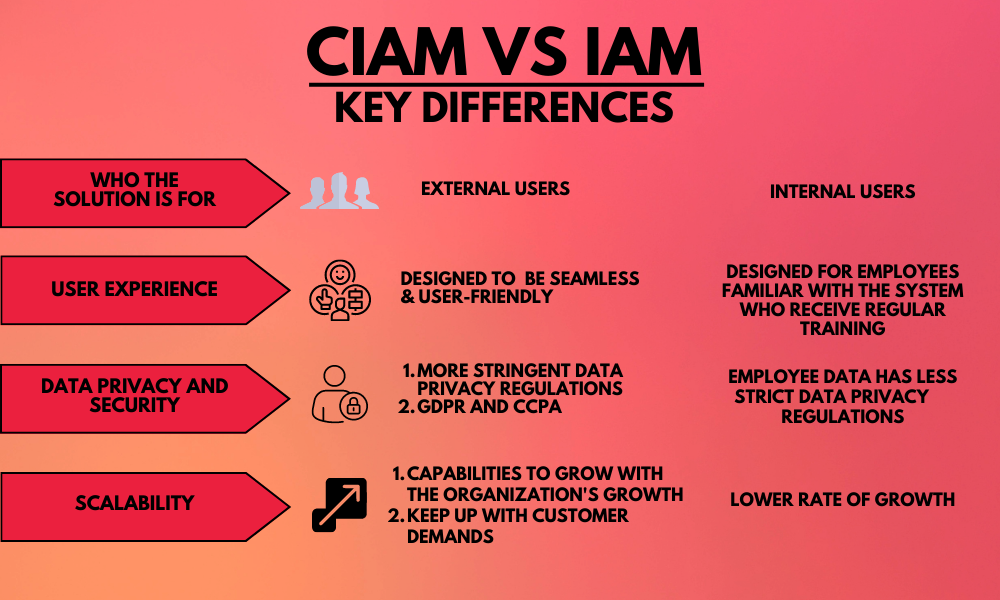
Who the Solution Is For
IAM solutions are primarily designed for managing internal users that require access to company applications and documentation.
CIAM solutions, on the other hand, are designed specifically for managing external users that are tailored to meet the unique needs and requirements of customer-facing applications and services.
User Experience
Another key difference between CIAM and IAM is the focus on user experience.
IAM solutions are designed for employees who are familiar with the organization’s framework and receive regular employee training.
CIAM solutions differ in that they are designed to provide a seamless user-friendly experience to external users with no training required.
Data Privacy and Security
Both IAM and CIAM solutions are designed to protect user data and provide secure access to resources.
However, CIAM solutions are often subject to stricter data privacy regulations, such as GDPR and CCPA, due to the sensitive nature of customer data.
Scalability
IAM solutions are designed for internal users. For most organizations, their rate of new employee onboarding isn’t that significant.
Compared with CIAM which is intended for customers and external users. The rate of new customers to an organization is usually exponential compared to employee growth.
Overall, IAM and CIAM share many similarities, however, there are key differences between the two solutions. Organizations that have both internal and external users may need to implement both IAM and CIAM solutions to meet their needs and ensure the security and privacy of their users’ data.
CIAM vs IAM: Use Cases
Both IAM and CIAM solutions can be used in a variety of industries.
IAM Use Cases
Employee management: IAM solutions are commonly used to manage employee access to internal resources and applications.
Compliance: IAM solutions help organizations ensure compliance with regulatory requirements by providing audit trails and access controls.
IT service management: IAM solutions streamline IT service management by automating user provisioning, de-provisioning, and access requests.
Healthcare: IAM solutions can be used to manage access to electronic health records and ensure the privacy and security of patient data.
CIAM Use Cases
E-commerce: CIAM solutions are commonly used in e-commerce applications to manage customer registration, authentication, and personalization.
Media and entertainment: CIAM solutions manage user access to media content, provide a personalized viewing experience, and enable social sharing and engagement.
Banking and financial services: CIAM solutions manage customer access to financial applications and services like online banking and mobile payments.
Travel and hospitality: CIAM solutions manage customer access to loyalty programs, reservation systems, and personalized travel experiences.
IAM solutions generally focus on managing internal users and resources, while CIAM solutions are designed to manage external users and provide a personalized and engaging experience.
Organizations should carefully consider their specific use cases and requirements when selecting an appropriate IAM or CIAM solution.
If you’re looking to improve your CIAM or IAM solutions or maybe you want more information on which would be the best fit for your organization speak to one of our experts today!
