
Phishing – 7 Tactics Hackers Use & How to Prevent Them
Not only that, the success of those attacks were up year-on-year by over 45%.
The result is a staggering increase in the volume and effectiveness of phishing attacks on both an individual and a company basis. Which is why it’s imperative that combating such attacks should be top of mind in any cybersecurity strategy.
Before discussing how security professionals can combat these attacks, let’s look at exactly what phishing is and various types of phishing to be aware of.
What is Phishing?
Phishing is the act of someone pretending to be a reputable business or individual to either directly coerce a user into revealing valuable information like their credit card details and passwords or plant malicious software on the user’s infrastructure.
Attackers usually attempt this by:
- Outright asking the user for sensitive information. For example, they may pretend to be a bank and asking for bank details and passwords for verification or send the user to a hoax website that resembles their bank or PayPal account where they are requested to input the information and their keystrokes are recorded
- Or the user receives a link that when opened plants malicious malware such as trojans or ransomware on the user’s device
In this article, we’ll dive into 7 specific types of phishing to be aware of:
Types of Phishing
1. Email Phishing
The most common form of phishing attempt that attackers use, email phishing involves the attacker curating an email to appear as though it is from a reputable source.
They do this by registering a fake domain that resembles a legitimate business. This fools recipients as, at a glance, a small difference from the reputable company’s domain may go unnoticed. For example, instead of using an ‘m’ they may use ‘rn’ to look similar or they may register a domain that is “<credible company name>support”.
By designing the email in the typical format of the credible company and including identical branding, users can be tricked into trusting the phishing email unless they more closely inspect the email address it came from.
2. Smishing
Similar to email phishing, smishing attackers use mobile phones as a platform to attack individuals. The attackers send out masses of messages to potential victims that appear as though they are from a reputable company in an attempt to extract personal information such as credit card details from the user.
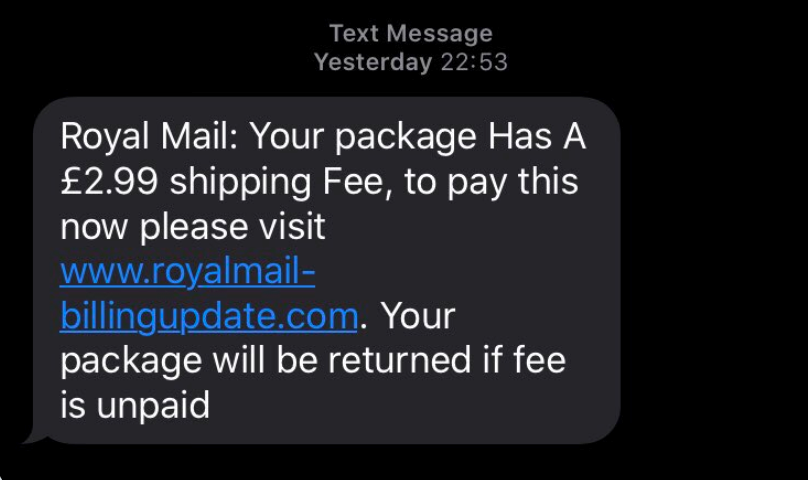
Text messages such as the one below claiming to be from Royal Mail (the British postal service) can fool consumers in this way. This particular SMS circulated in the UK following the surge in online shopping during the covid-19 pandemic.
3. Search Engine Phishing
In search engine phishing attacks, users are presented with offers or messages to lure them into clicking bad links. The attackers create fake websites and get indexed on legitimate search engines like Google to then lure consumers to enter their personal information and/or payment information to purchase deals.
Google reported that they detected 25 billion spammy pages every single day in 2020.
4. Vishing
Vishing scams use phone calls to defraud victims. The attacker calls their target, claiming to be a representative from a bank or other reputable institution in an attempt to extract personal information or even have them directly wire money right then over the phone.
Attackers take advantage of events to appear more persuasive and legitimate to their victims. For example, during tax season fraudulent callers whereby the caller impersonates an IRS representative are much higher because they’re more likely to be believed at this time of year.
5. Angler Phishing
In this relatively new method of phishing, attackers target social media users by posing as a customer service agent in an attempt to extract personal information from unhappy customers of a product or service.
Attackers create a fake account on platforms such as Twitter, Facebook or Instagram, ensuring that the fake account resembles a legitimate business page. The attacker then targets users who have publicly shared their unhappy feelings about a product or service the brand offers.
The fake account directs the victim to a link to connect with an agent and resolve their issue. In actual fact, that link will plant malware on the victim’s device or send them to a website that will attempt to extract information or money from them.
6. Spear Phishing
Rather than generic email phishing sent out at scale in the hopes that some recipients will fall for the scam, spear phishing is more targeted attempts to defraud specific individuals within an organization.
These emails are often more personalized and include believable context to lure the victim into trusting the sender. For example, the attackers may compromise the email of someone else in the organization, observe the conversations, and use this information to target someone else in the organization.
7. Whaling
Whaling, although very similar to spear fishing, only targets “big fish” in the organization such as c-suite executives rather than lower level employees – individuals who have access to more highly valuable and confidential information about the organization. If targeted as a specific executive level individual, email phishing, vishing, and smishing can all incorporate whaling tactics.
Tessian reported that in November 2020, the co-founder of Levitas Capital, an Australian hedge fund, followed a fake Zoom link that installed malware on the company network. The attackers attempted to steal $8.7 million using fraudulent invoices. They only got away with $800,000 but the reputational damage was done. Levitas lost its biggest client and ultimately closed.
Phishing Prevention – Keep Your Company and Employees Safe
Training and Awareness
Initiatives training employees to detect phishing messages, spot fraudulent links, assess whether the website they are using is secured, and make judgements on when to share personal or company data is absolutely critical.
This awareness could be the difference between reputational damage and financial losses versus safeguarding the cybersecurity of your employees and customers.
In fact, Microsoft reported seeing a 50% year-over-year reduction in employee susceptibility to phishing after simulation training.
However, more than 80% of companies surveyed by Proofpoint in 2022 said that at least half of their employees are working remotely due to the COVID-19 pandemic but less than half said they educate workers about best practices for remote working. The result is a workforce highly susceptible to cyber attacks, including phishing.
Keep Software Updated
The latest software updates for your operating system and applications across all devices will help protect your organization from any attacks. For example, malware sent in a phishing email and downloaded by an employee could be blocked by the latest update of your software, versus an older version not equipped with the right patches to combat the attack.
Check out our full article on Software Updates: Why They Matter to Your Cybersecurity.
Implement Multi-Factor Authentication
Multi-factor authentication requires multiple pieces of information for your customers or employees to login, and is an essential part of your identity and access management solution.
This helps protect against phishing attacks that convince the recipient to disclose their login credentials. The victim may disclose their username and passwords, but biometric data is much harder for the attacker to steal or replicate, rendering their phishing attack useless.
If you’re struggling to implement the most secure identity and access management solution for your business, RediMinds are the certified security implementation partner you can trust.
With a dedicated team, sharing years of experience implementing solutions like Transmit Security and Okta, we will help you define and execute the right solution that provides the highest level of protection for your employees and customers.
Get in touch today to find out how.
